CMMC: Safeguarding the Future of U.S. Defense Contracts
In today’s interconnected world, cyber threats are sophisticated and increasingly pervasive. The U.S. Department of Defense (DoD) depends on thousands of contractors—ranging from large corporations to small businesses—to deliver critical technologies and services, many of which involve sensitive information. Unfortunately, these contractors have become prime targets for cyberattacks. Recognizing the urgent need to bolster cybersecurity across its entire supply chain, the DoD implemented the Cybersecurity Maturity Model Certification (CMMC).
In its 2.0 iteration, CMMC introduces structured, enforceable cybersecurity standards designed to protect sensitive information, ensure consistent compliance, and strengthen the defense supply chain. But why was CMMC necessary? Let’s explore the key drivers behind its creation.
Key Features of CMMC 2.0
- Tiered Model: Aligns cybersecurity standards with the sensitivity of information, ensuring appropriate levels of protection throughout the supply chain.
- Assessment Requirement: Mandates third-party assessments for companies handling CUI, verifying compliance through certified organizations.
- Implementation Through Contracts: Requires CMMC certification as a prerequisite for bidding on certain DoD contracts, reinforcing cybersecurity as a non-negotiable standard. Subcontractors must also have minimum CMMC status.

1. Addressing Rising Cybersecurity Threats in Defense Contracting
The Defense Industrial Base (DIB) has seen a dramatic rise in cyberattacks over the past decade. State-sponsored actors and cybercriminals have increasingly exploited vulnerabilities in contractors’ networks to steal Controlled Unclassified Information (CUI). Though not classified, CUI holds immense strategic value, including blueprints, research data, and specifications that, if compromised, can give adversaries a tactical advantage.
CMMC ensures that protecting CUI is not just the responsibility of individual contractors but a collective mandate for national security. Through clear standards, the program requires robust cybersecurity practices regardless of the contractor’s size.
2. Standardizing Cybersecurity Practices Across the Supply Chain
Before CMMC, defense contractors self-assessed compliance with the National Institute of Standards and Technology (NIST) Special Publication 800-171 framework. However, these self-assessments varied widely in quality. Many contractors needed more expertise or resources to evaluate or implement the required security controls accurately, creating gaps across the defense supply chain.
CMMC addresses this issue by mandating third-party assessments through Certified Third-Party Assessment Organizations (C3PAOs). C3PAOs eliminate inconsistencies and ensure a reliable, uniform cybersecurity standard across the defense industrial base. Contractors are no longer solely responsible for determining their readiness—certification is now externally validated to prevent weak links in the supply chain.
3. Securing National Defense Through Tiered Certification Levels
Small and medium-sized contractors are especially vulnerable to cyberattacks due to limited cybersecurity resources. However, these companies are often deeply involved in critical defense projects, making them attractive targets for adversaries.
- CMMC 2.0 introduces a tiered certification model, as shown in Table 1, aligning required security practices with the sensitivity of the information handled:
- Level 1 (Foundational): This level focuses on basic cybersecurity hygiene for contractors managing less sensitive data. It requires an annual self-assessment with a senior executive’s affirmation of compliance.
- Level 2 (Advanced): Introduces two categories of assessment based on the type of CUI handled. It aligns closely with NIST 800-171 standards and applies to contractors handling CUI.
- High Importance Programs (Critical National Security Information): Requires a C3PAO assessment.
- Less Sensitive Programs: Contractors conduct an annual self-assessment with a senior executive’s affirmation of compliance.
Level 3 (Expert): Designed for companies managing the most sensitive information related to national security, requiring more advanced controls. It requires a pre-requisite C3PAO assessment for Level 2 High and a Defense Contract Management Agency (DCMA) Defense Industrial Base Cybersecurity Assessment Center (DIBAC) assessment.
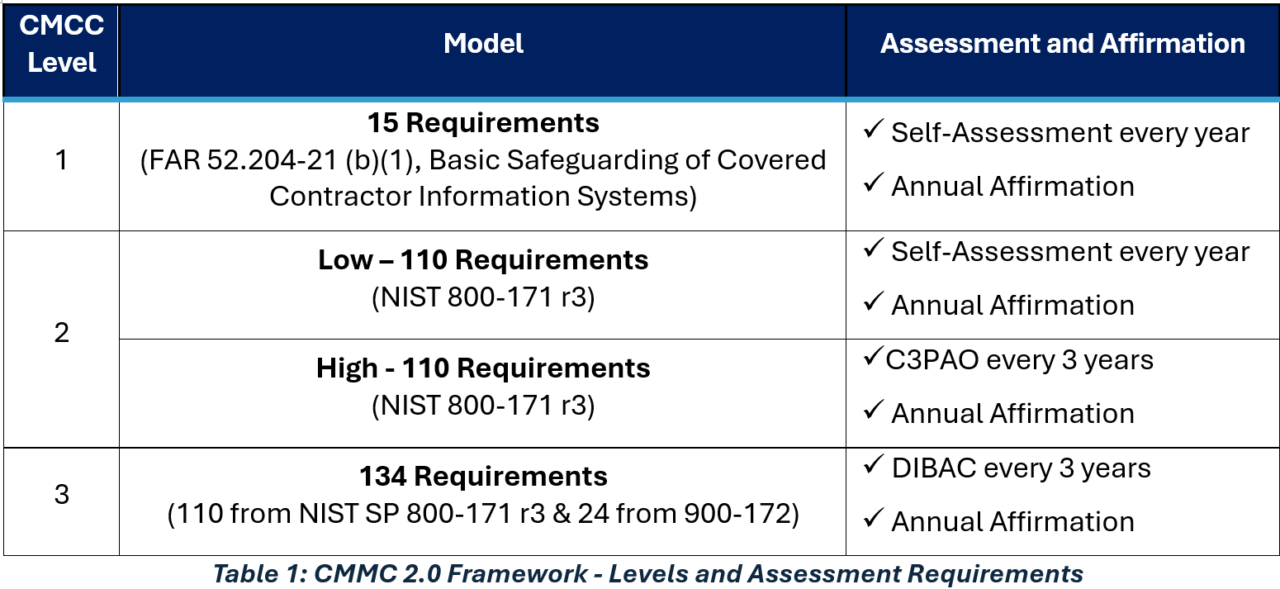
This structured approach ensures that contractors handling highly sensitive information meet more stringent requirements, while smaller contractors can focus on appropriate protections relevant to their role.
4. Accountability Through Third-Party Certification
CMMC introduces accountability and enforcement, which were previously absent from defense contracting. Under the new model, contractors at Levels 2 (Advanced – High) and 3 (Expert) work with C3PAOs for impartial certification assessments.
The DoD ensures cybersecurity becomes a top priority by tying CMMC certification to contract eligibility. Contractors that fail to meet the required certification level are ineligible to bid on DoD contracts. This “no certification, no contract” policy motivates organizations to invest in their cybersecurity, fostering a culture of compliance across the defense industry.
5. Securing the Entire Defense Supply Chain
With more than 300,000 organizations comprising the defense industrial base, a single weak link can jeopardize national security. CMMC takes a holistic approach, requiring not only prime contractors but also subcontractors to meet the appropriate level of cybersecurity.
This standardized cybersecurity enforcement across all supply chain tiers closes the gaps that adversaries previously exploited. The program strengthens the entire defense ecosystem by ensuring that every contractor, from the smallest subcontractor to the largest corporation, adheres to consistent standards.
Conclusion: A New Standard for Cybersecurity in Defense Contracting
The Cybersecurity Maturity Model Certification marks a significant shift in the DoD’s approach to cybersecurity. By addressing increasing cyber threats, standardizing security practices, and requiring third-party assessments, the DoD proactively protects its supply chain and secures sensitive information critical to national defense.
For contractors, CMMC is both a challenge and an opportunity. While it raises the bar for cybersecurity, it also creates a competitive advantage for companies that achieve certification. Those who proactively embrace CMMC position themselves as trusted partners in defense, opening doors to new contracts and opportunities.
As the DoD begins to roll out CMMC requirements across all DoD contracts, companies are highly encourgaged to invest in cybersecurity now to secure their future and contribute to the national defense mission, ensuring that sensitive information stays out of the wrong hands.
References
These sources offer the foundational details about CMMC and its relevance in government contracting.
- U.S. Department of Defense (DoD) CMMC Portal.
CMMC Model & Overview https://dodcio.defense.gov/CMMC/Model/
- National Institute of Standards and Technology (NIST) Special Publication 800-171.
SP 800-171 Publication https://csrc.nist.gov/pubs/sp/800/171/r3/final
